Cyber-monitoring tools:

In this technology-driven era, there is a real battle between cybercriminals and those of us who aim to protect against them. As the bad guys continue to increase their skills and tactics, we must strengthen our defences. At the core of our digital fortress lies a potent weapon: cyber-monitoring tools. In this world of cyber-guardians, we will explore how these tools are instrumental in securing our networks, detecting threats, and more.
Cyber-Monitoring Tools: Understanding the Fundamentals of Network Security
These are the fundamental concepts and principles of securing computer networks from unauthorised access, misuse, modification, or denial of service attacks. It involves implementing various security measures, such as firewalls, intrusion detection systems, encryption, and access controls, to protect networks and their data from cyber threats. Understanding network security is crucial for businesses, organisations, and individuals who want to safeguard their valuable information and ensure the confidentiality, integrity, and availability of their network resources.
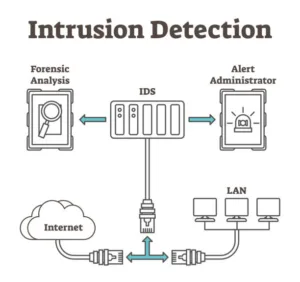
Let’s meet the heroes: intrusion detection systems (IDS) and intrusion prevention systems (IPS). They’re the Sherlock Holmes and action heroes of the cybersecurity world. These tools act as watchmen, scanning network traffic for unusual patterns that may hint at intruders. Once something suspicious is detected, alarms go off, and the gates are quickly shut to keep the bad guys out. Think of them as your 24/7 digital bodyguards.
Read More: Your Essential Guide to Understanding Cyber Monitoring
Cyber-Monitoring Tools: The Detectives of the Digital World

“Our cyber warriors are not just responsible for network security. They play the role of digital detectives who keep a watchful eye on any dubious activities. They are supported by a powerful ally called the Security Information and Event Management (SIEM) system. Think of SIEM as a puzzle solver that gathers data from network traffic, logs, and devices to provide a clear picture of what’s happening in your digital kingdom. SIEM not only observes but also automates the response to security incidents. In the event of a cyber threat, it can take immediate action to prevent any actual damage. This is what we call next-level vigilance!”
Cyber-Monitoring Tools: Your Trusted Bodyguards
As we move towards a more digital life, our networks and devices need to be safeguarded against cyber threats. This is where “endpoint detection and response (EDR) tools” come into play. Consider them as personal investigators for your desktops, laptops, and mobile devices. They operate in the background, monitoring your devices for any suspicious activity. In the event of any unusual behaviour, they will promptly alert you or isolate the offender. It’s like having a team of superheroes dedicated to protecting your devices.
Cyber-Monitoring Tools: Knowledge is Power
Knowledge is powerful, and that’s where threat intelligence comes into play. Our team of cyber guardians always stays ahead of the game by using their intelligence. It’s like having an insider who whispers about the bad guys’ plans.
Threat intelligence is all about collecting information on current and emerging threats. It’s like knowing the bad guys’ playbook. With this information, our cyber defenders can customise their strategies to thwart specific threats and vulnerabilities. It’s like having a secret weapon that helps us focus on what truly matters.
Facing the Unknown with Cyber-Monitoring Tools

In the realm of cybersecurity, the unknown always poses a lurking danger. This is where cyber-monitoring tools come into play, particularly in security incident response. They act as your quick-response team, ready to take action when the alarm bells go off.
These tools not only identify threats but also assist in tracking them back to their origins. This kind of understanding is essential for developing a targeted defence. Additionally, they can automate the response process, significantly reducing the time it takes to contain and counteract threats. It’s similar to having a fire brigade that responds before the fire spreads.
Read More: Unravelling the Positive Power of Cyber Monitoring in Today’s Cybersecurity
Conclusion
In a world where cyber threats are real and ever-present, having these tools in your arsenal is not just a choice; it’s a necessity. So, whether you’re a tech wizard or just someone who wants to keep their digital life safe, remember that cyber monitoring tools are your best friends in this digital adventure. They are the heroes of the digital realm, silently working day and night to keep you, your data, and your digital kingdom safe. So, stay informed, stay vigilant, and keep your digital fortress strong with these trusty companions by your side.
In a nutshell, cyber monitoring tools are our knights in shining armour in this endless battle between good and evil in the digital realm. From protecting our network to investigating potential threats and securing our devices, they are our silent guardians. They are the ones who stand between us and the chaos of the cyberworld. In a world where technology evolves at breakneck speed, our cyber tools keep up the pace, adapting and evolving to stay one step ahead of those who seek to breach our digital fortresses.










